firegopher / docs
Architecture
The firegopher project is made up of three main parts:
- The VM Runner, which prepares the host system and starts the guest VM
- The Guest Init System, which runs inside of the guest VM and starts the user workload
- A set of customised root filesystems (Base Images) to be used for the guest VM and an Asset Manager to install and manage them
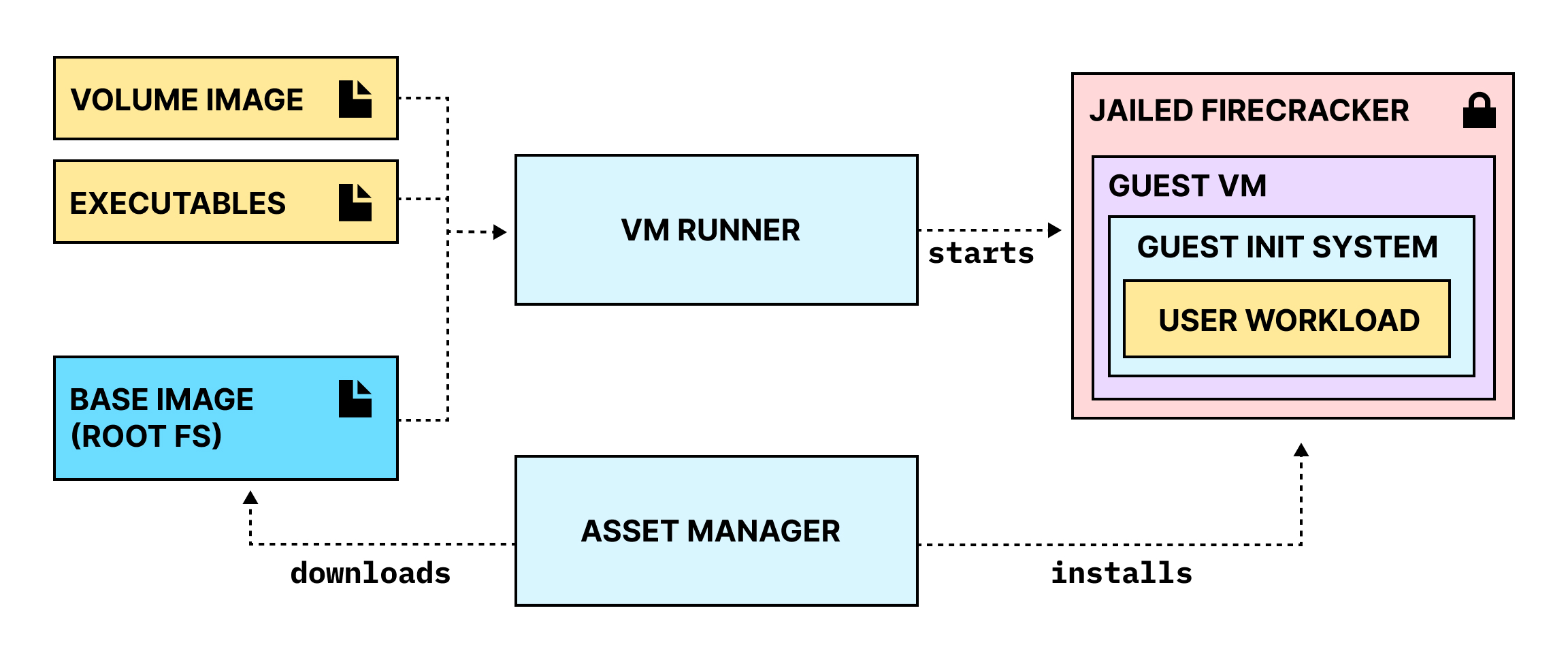
VM Runner
The VM Runner has four main responsibilities:
- It prepares the root file system for the guest VM
- by unpacking the user assets into a copy of the chosen Base Image
- and creating a configuration file that instructs the Guest Init System on what to do with them
- It prepares the Firecracker Jail
- by first creating a directory that will later be used by the Firecracker Jailer as a CHROOT root directory
- and copying/hardlinking all the assets that are needed to run the guest VM into it
- It creates and configures the network device needed for the guest VM
- It starts the jailed Firecracker process and supervises it
Guest Init System
The Guest Init System is a barebones init system specifically designed to run a single application inside of a VM. At its core it is a go-rewrite of fly-init-snapshot.
The main responsibilities of the guest init system are:
- reading the configuration passed to it from the VM Runner
- mounting the root file system
- mounting all the required device files
- configuring the network interface
- dropping root privileges
- starting the user workload and supervising it
Asset Manager
The Asset Manager is currently in the early stages of its development. In its current state it is little more than a glorified download script.
It downloads the following assets:
- A Linux Kernel Image
- A specific version of Firecracker (currently 1.6.0)
- A modified version of the Ubuntu 22.04 root file system
Base Images
Currently there is only one officially supported base image available to be used with firegopher. It is a slightly modified version of Ubuntu 22.04 Minimal. The modifications that are currently done to create the finished base image are:
- Installing
ca-certificates,curlandpython3 - Clearing out the existing package lists afterwards by deleting all files in
/var/lib/apt/lists/
The current base image creation process is heavily based on the process outlined by the Firecracker team here.
Networking
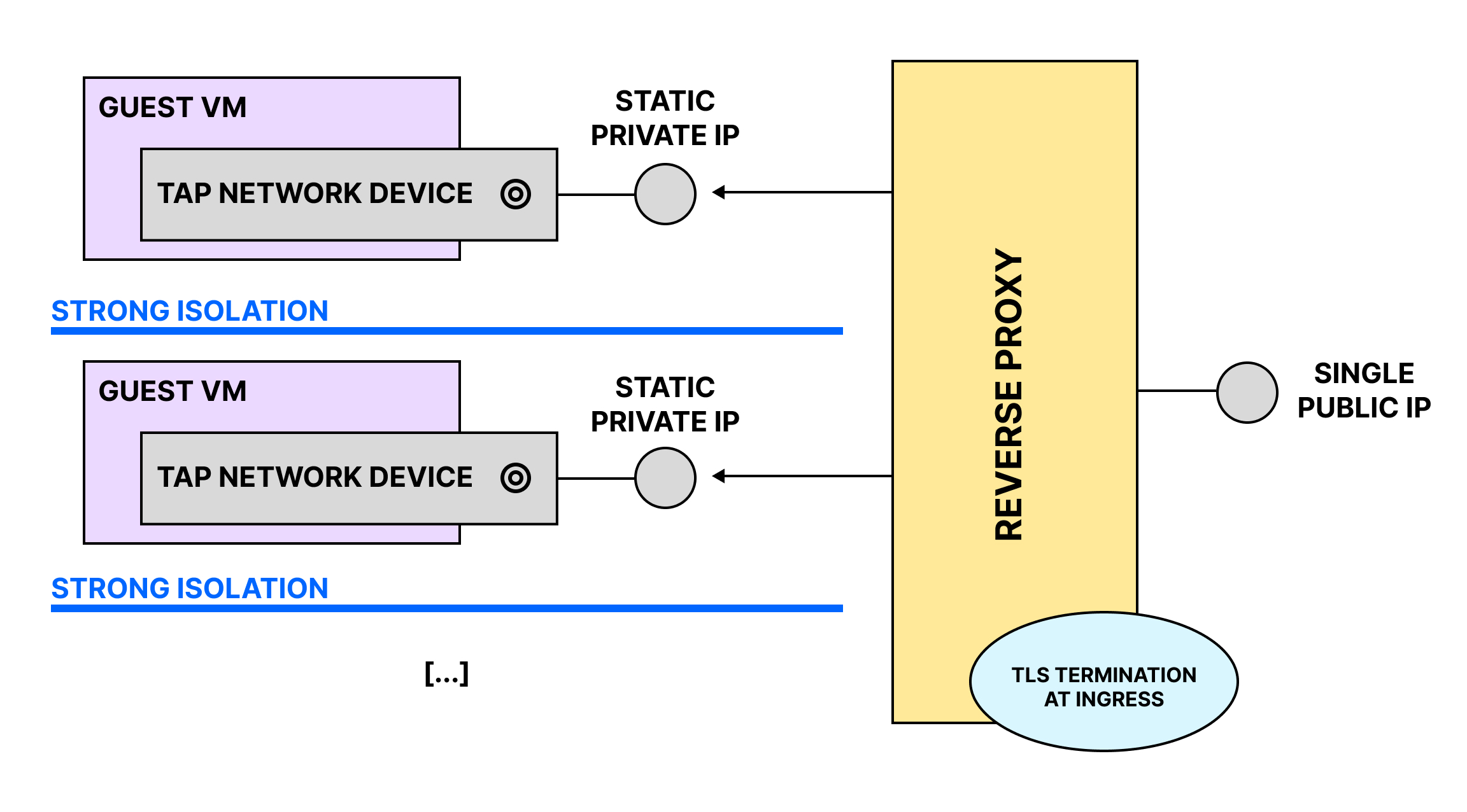
The current networking setup is in its very early-stages and should not be considered stable.
Firegopher is designed to be used with a reverse proxy on the host machine that routes incoming traffic to the different running microVMs. In the future Firegopher will automatically configure a reverse proxy based on the users needs. Currently users need to configure a reverse proxy manually.
Currently every microVM is automatically assigned a non-internet-routable IP in the range 172.19.0.0/16. The host system is instructed to forward all traffic from the microVM to the internet.